Information Security and Protection of Personal Information
Information Security and Protection of Personal Information
1. Information Security and Personal Information Protection System
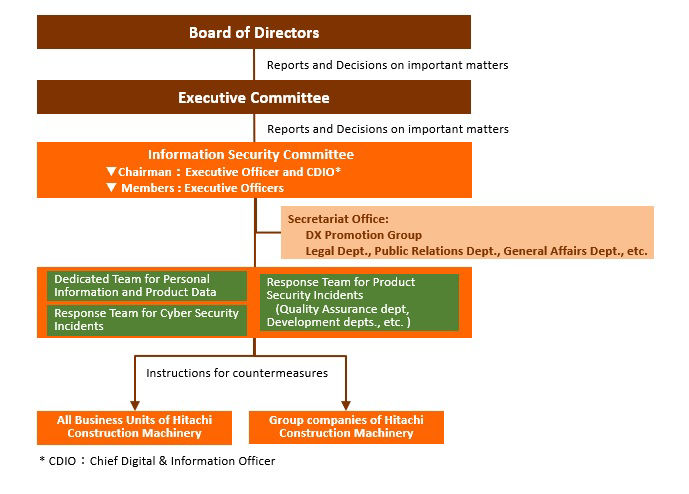
Hitachi Construction Machinery’s Chief Information Security Officer is appointed by the company’s president out of Executive Officers and has the authority and responsibility to implement and operate information security measures.
The Information Security Committee, chaired by the Chief Information Security Officer determines policies and procedures for information security and personal information protection. Secretariat of the Information Security Committee conveys decisions internally and to other companies in the Hitachi Construction Machinery Group. Information Security Officers at business units and companies ensure that these decisions are implemented in the workplace.
Information Security Posture (Team Structure)
The Hitachi Construction Machinery Group emphasizes two points in information security and personal information protection:
2. Information Security and Personal Information Protection Initiatives
2.1 Basic Approach to Information Security Governance
a. Clearly designate assets to be protected
•Evaluate information assets and conduct risk analysis
b. Improve user literacy
•Develop security education materials
•Educate managers and staff
c. Implement preventive techniques
•Widely implement administrative measures
•Deploy technological processes
d. Establish information security posture
•Develop rules (security policies)
•Develop security management posture
•Establish audit and follow-up system
•Ensure solid feedback through extensive PDCA cycles for preventive and incident response processes
2.2 Preventing Information Leakage
Hitachi Construction Machinery Co., Ltd. has formulated the Three Principles for Preventing Leakage of Confidential Information to ensure the highest level of care for such information and to prevent leakage and other related incidents.
Our policies ensure that if an incident does occur, we strive to minimize the damage by contacting customers promptly, investigating causes, and acting to prevent any recurrence.
We take the following IT measures to prevent information leakage: using encryption software and secure PCs; deploying electronic document access control; maintaining ID management and access control by building an authentication infrastructure; and filtering e-mails and visited websites. In response to the recent spate of targeted e-mail attacks and other cyberattacks, We are also improving our countermeasures by adding more layers to our leakage protection methods, including those at both the entry and exit points of our network.
To ensure the secure exchange of information with our suppliers, we review their information security measures based on Hitachi Construction Machinery’s own standards before allowing them access to our confidential information. In addition, in order to prevent information leakage from suppliers (procurement partners), we have provided them with tools for checking business information on information devices as well as security training materials and request them to inspect and delete business information on personal devices.
[Three Principles for Preventing Leakage of Confidential Information]
Principle 1 As a general principle nobody can take Confidential Information out of the Company’s premises.
Principle 2 Any person taking Confidential Information out of the Company’s premises due to business necessity shall obtain prior approval from the Information Asset Manager.
Principle 3 Any person taking Confidential Information out of the Company’s premises due to business necessity shall put in place relevant and appropriate measures against information leakage.
2.3 Information Security Education and Training
To consistently maintain level of information security, it is critical for each and every one of us to strive daily to acquire the knowledge needed for handling information and to remain strongly aware of issues. To this end, we conduct e-learning trainings on information security and personal information protection every year for all directors, employees, and temporary employees.
Furthermore, we offer a variety of courses that are tailored to different target audiences, including new employees, new managers, and information system administrators. Since 2014, we also carry out simulation training to educate employees about the increasing trend toward malicious targeted e-mail attacks and other cyberattacks. Employees are sent examples of targeted e-mail to heighten their awareness of security through direct experience.
Our education and training programs are available to Hitachi Construction Machinery Group companies in Japan and other global regions and we actively working on education and trainings on information security and personal information protection as a whole group of Hitachi Construction Machinery.
2.4 Thorough Information Security Audits and Inspections
Hitachi Construction Machinery have been promoting information security activities by the “plan-do-check-act” (PDCA) cycle for information security management system. We conduct self-audits both for information security and personal information protection in each Group company or business unit on a yearly basis.
For Hitachi Construction Machinery Group companies outside Japan, we use a “common global self-check” approach to ensure Group-wide auditing and inspections. We implement Confirmation of Personal Information Protection and Information Security Management annually for the voluntary inspection of business unit workplaces.
2.5 Information Security Business Continuity Plan (IT-BCP)
Preparing for future cyber attacks and damage caused by natural disasters which have been increasing in recent years, we at Hitachi Construction Machinery have been developing Information Security Business Continuity Plan (IT-BCP). In order to minimize the possible harm caused by disasters, we have been working on integration of core systems and migration to virtual servers or the cloud. As preparation for a disaster, we design the operation which allows us to restore the systems within a predefined timeframe and conduct a system-recovery-drill one a year.
Also, aiming at enhancing resilience of our information systems against cyber attacks, we have been supporting initiatives such as server enhancement and separation of factory networks.
2.6 Rolling out Information Security Management Globally
Hitachi Construction Machinery group companies worldwide have revised the regulations based on the Cybersecurity Framework issued by the National Institute of Standards and Technology (NIST), responding to cyber threats and reinforcing their information security.
These rules are distributed from the parent company in Japan to Group companies around the world. We are taking security measures by thoroughly enforcing security governance in our group companies.
Hitachi Construction Machinery has established the “Products and Services Data Governance Subcommittee” as a subordinate organization of Information Security Committee and started its activities in 2021. This aims to globally promote protection and utilization of the data owned by Hitachi Construction Machinery, including the operational data of our products. In this organization, we are trying to work on establishment of global policies, development of unified standards for data protection safeguards to be implemented in products and services, and monitoring their operation status, and evaluating their effectiveness.
Through these activities, we will continue to strive to develop products and provide solution services by utilizing data as well as to ensure appropriate data risk management and the continued trust of stakeholders.
2.7 Cyber Security
2.7.1 Prevention of information security incidents
Hitachi Construction Machinery implements robust security measures against the risk of cyberattacks and information leaks. In addition to taking appropriate defense measures at each layer of the network, servers, and endpoints, we are working to strengthen vulnerability management and monitoring systems. In addition, in order to ensure the protection of information assets and business continuity, we regularly conduct risk assessments and review security measures to maintain a safe IT environment.
2.7.2 Computer / Cyber Security Incident Response Team (CSIRT)
Hitachi Construction Machinery has established the Hitachi Construction Machinery -CSIRT, a specialized team responsible for responding to cyberattacks, and is promoting security measures in normal times and emergencies. In July 2023, Hitachi Construction Machinery-CSIRT became a member of NCA (Nippon CSIRT Association), engaging in activities in collaboration with external organizations’ CSIRTs within Japan to enhance its operational capabilities.
In normal times, we are working to strengthen internal security by disseminating security information, responding to vulnerabilities, monitoring systems, and conducting education and training. In the event of a cybersecurity incident (in case of emergency), we work with the Information Security Committee to promptly investigate, respond, and recover, as well as formulate and disseminate measures to prevent recurrence.
3. Our Initiatives for Product Security
Security for products and solutions that HCM provide to customers is getting more important than ever. In order to address this, we have a Response Team for Product Security Incidents established, which works closely with the Information Security Committee. The Response Team for Product Security Incidents also works with the Response Team for Cyber Security Incidents. We take countermeasures in each area, while sharing information between the teams, when any information is received by either team.